Recently I was trying to integrate Snowflake to SSO with G-suite and I went through a world of pain to get it working. The documentation was out of date and did not help with 403 error that I was continuously receiving. I have therefore written this blogpost, hoping it would help someone else in the future.
G-Suite Setup
To get started you first need to create a new SAML app in G-suite. You may require admin access to perform this action:
Login to https://admin.google.com and click on the three lines to open the menu
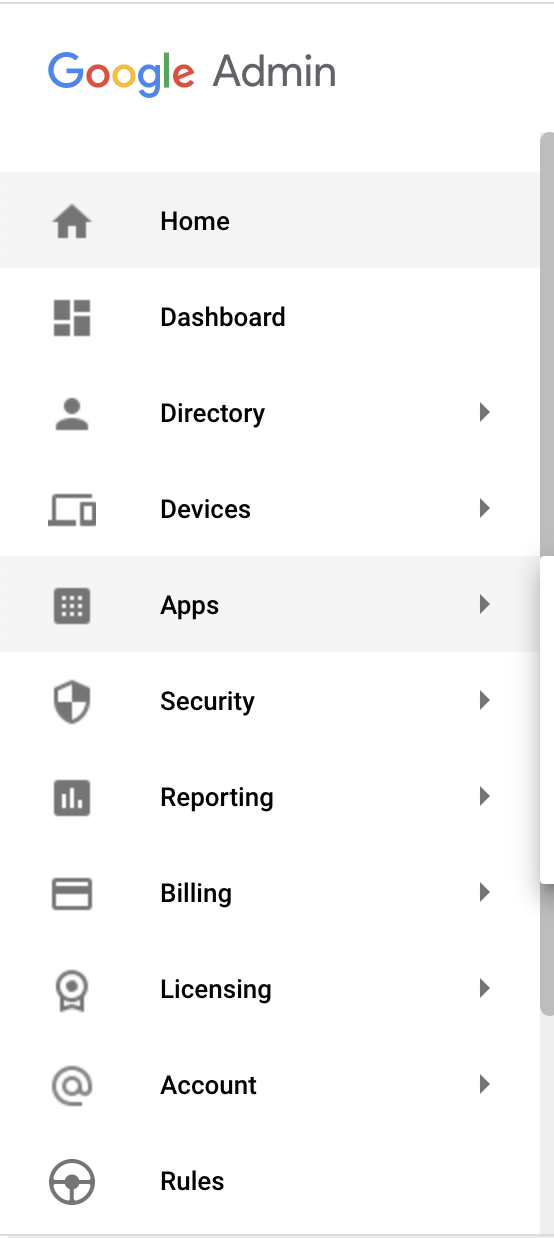
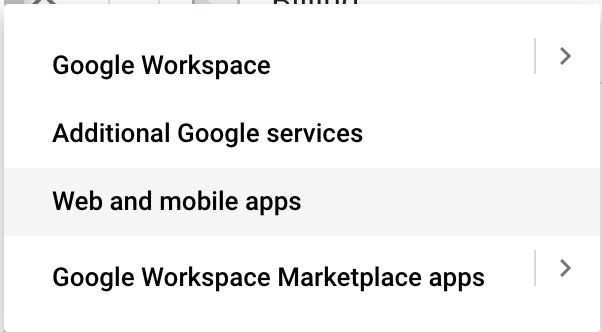
From the menu click on the Apps and select Web and mobile apps
Click on Add App then Add custom SAML app
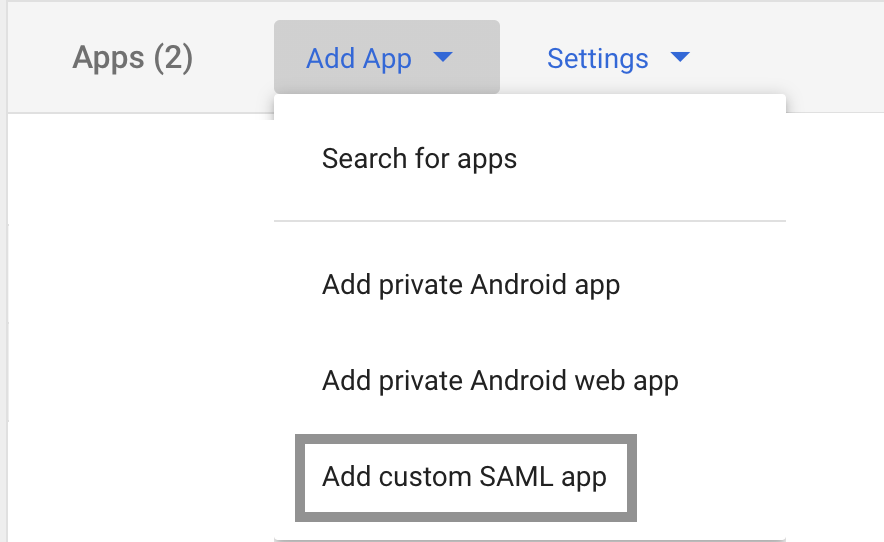
Enter your app details and press continue
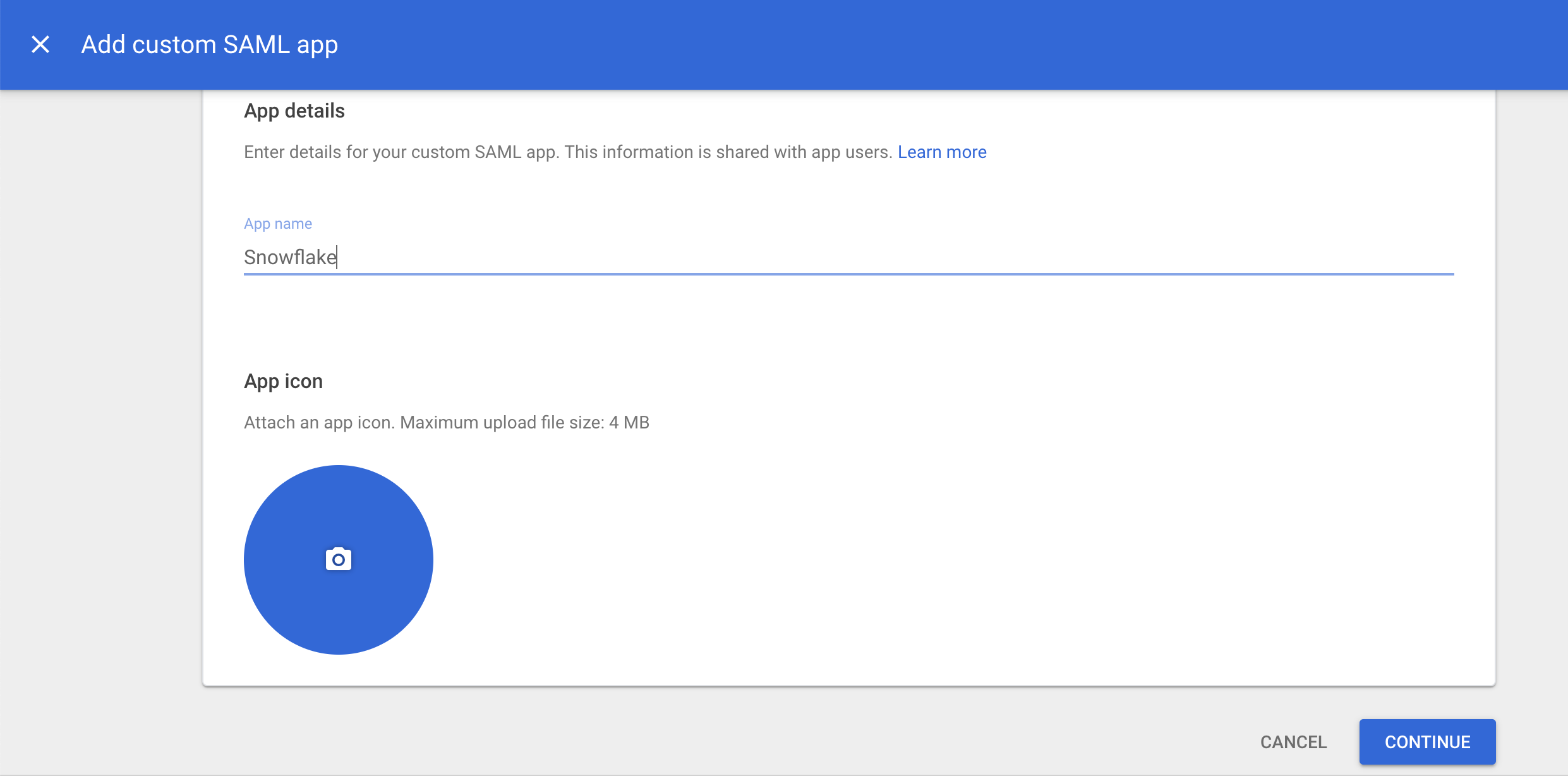
Copy the values of SSO URL , Entity ID and Certificate and click continue. You will need those later when setting up Snowflake
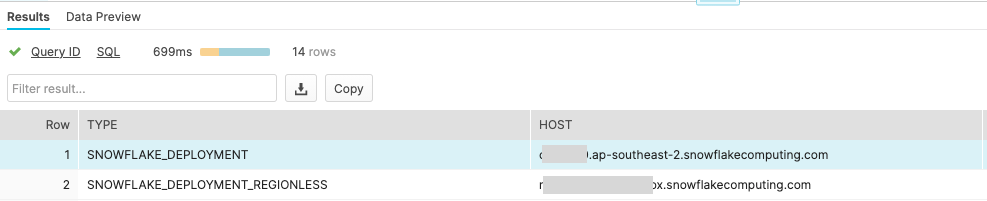
Recently Snowflake has introduced a friendly name for the account, however in order to setup SSO with G-Suite you need Snowflake's auto generated account name and region. To retrieve your generated account name run below command in Snowflake.
select t.value:type::varchar as type,
t.value:host::varchar as host,
t.value:port as port
from table(flatten(input => parse_json(system$whitelist()))) as t;
The regional account name will be in the SNOWFLAKE_DEPLOYMENT field
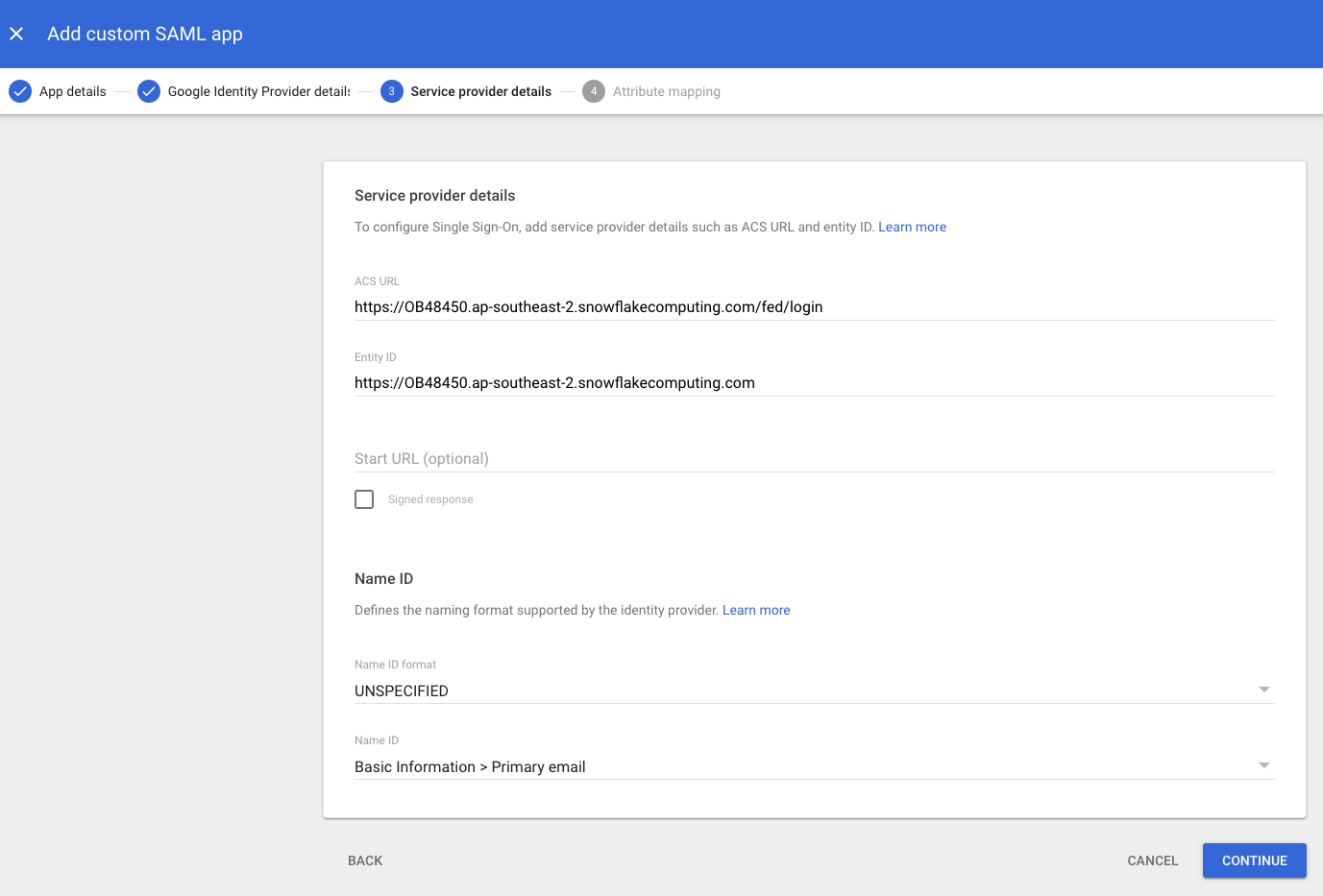
Back in G-suite enter the Service provider details as below and press Continue. ACS URL:
https://${regionalAccountName}.{region}.snowflakecomputing.com/fed/login
Entity ID:
https://${regionalAccountName}.{region}.snowflakecomputing.com
Note! Make sure there are no trailing slashes in ACS URL or Entity ID
You do not need to change anything in attribute mapping, click Finish
One last step left in G-suite is to enable your users for this app. To do this click on the User access inside your app
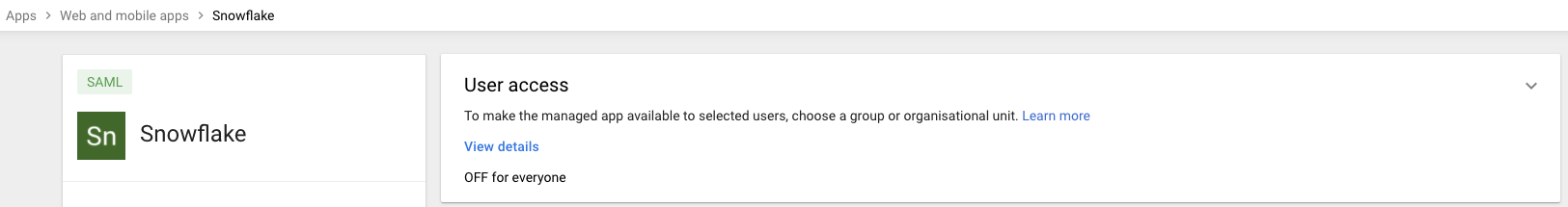
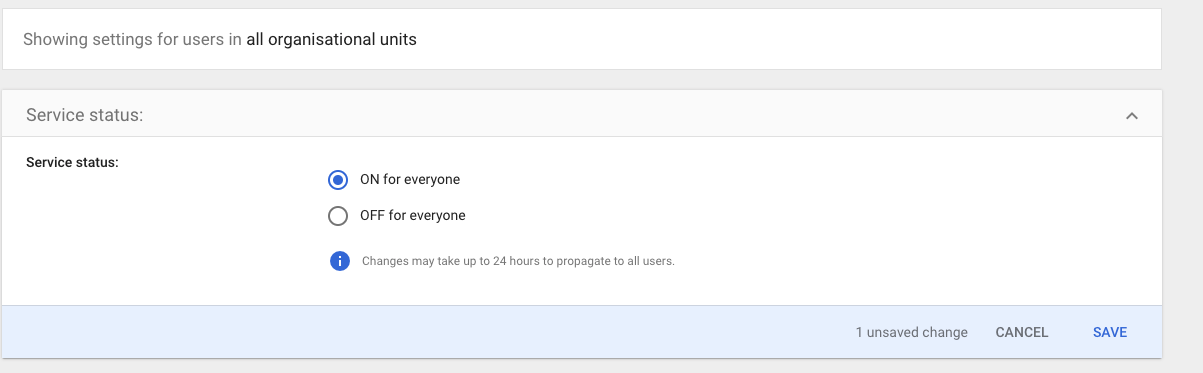
Make sure to turn it on for everyone and click on save. Alternatively, you could turn it on for a specific group of users
Snowflake Setup:
Now go to your Snowflake account and set saml_identity_provider on the account level. Replace the certificate, issuer and ssoUrl with values copied from G-suite app and run below commands.
Note!
- When entering the certificate into Snowflake please ensure the certificate is ALL ON ONE LINE (e.g. no carriage returns) along with remove the Begin and End Certificate tags
- Issuer value will be from entity ID in your G-suite app
- Run below commands using AccountAdmin role
alter account set saml_identity_provider = '{
"certificate": "MIIDdDCCabhduknsykgIGAWt...UV6+gsftmCsM",
"issuer": "https://accounts.google.com/o/saml2?idpid=Cdummy045",
"ssoUrl": "https://accounts.google.com/o/saml2/idp?idpid=Cdummy045",
"type" : "Custom",
"label" : "gsuiteSingleSignOn"
}';
alter account set sso_login_page = true;
Verify your connection:
Unfortunately automatic provisioning with G-suite does not work in Snowflake. Therefore you will have to manually create your users in Snowflake. Run below command to create your users using their email addresses:
Note! You do not need to specify passwords for SSO users in Snowflake
CREATE USER "zainab.maleki@mechanicalrock.io";
Once all the above setup is completed, now you can test your integration using the below URL:
Note! If you change any settings, verify it in a cognito browser as I noticed G-Suite sometimes returns cached response
https://${Your account friendly name}.snowflakecomputing.com/console/login?fedpreview=true
If you need any help with your Snowflake setup, patterns and best practices, feel free to get in touch.
